Deploying a sample application
In this course, we will deploy a sample application, review it and then secure it with a policy compliant certificate.
This course starts with a deployment of a sample application. If you choose to use an application of your choice or have something already deployed, you can skip the deployment instructions.
In terms of objectives, this course will cover
- Deployment of an app and reviewing the various resources (Deployment, Service)
- Creating an Ingress
- Introduction to Certificate resource and associating it with Ingress
- Navigating TLS Protect for Kubernetes to inspect the certificate and ingress resource to ensure it is configured correctly
Some assumptions:
- An ingress controller is deployed on the cluster
- You have the ability to update the DNS records to map a domain to the ingress controller's external IP or host.
The TLS Protect for Kubernetes Integration catalog provides detailed information for some of the popular ingress controllers and instructions to configure them.
Hello, world!
In our previous course that focused on creating an issuer, we used a namespace called jss-academy for creating an Issuer. We will use the previously created issuer to request a Certificate. If you need to recreate the Issuer follow the course Creating and configuring Issuers
Apply the below configuration to create hello-jss-app in your cluster.
cat <<EOF | kubectl apply -f -apiVersion: apps/v1kind: Deploymentmetadata:labels:app: hello-jssname: hello-jss-appnamespace: jss-academyspec:replicas: 3selector:matchLabels:app: hello-jsstemplate:metadata:labels:app: hello-jssspec:containers:- image: gcr.io/google-samples/hello-app:1.0imagePullPolicy: IfNotPresentname: hello-jss---apiVersion: v1kind: Servicemetadata:labels:app: hello-jssname: hello-jss-svcnamespace: jss-academyspec:ports:- port: 8080protocol: TCPtargetPort: 8080selector:app: hello-jsssessionAffinity: Nonetype: ClusterIPEOF
Before creating an Ingress, let's confirm that an ingress controller is installed. In this course, we will use NGINX Ingress controller. For more details about how NGINX Ingress controller works with Jetstack Secure, checkout TLS Protect for Kubernetes Integrations.
You can check the version of NGINX Ingress controller by simply running
POD_NAMESPACE=ingress-nginxPOD_NAME=$(kubectl get pods -n $POD_NAMESPACE -l app.kubernetes.io/name=ingress-nginx --field-selector=status.phase=Running -o jsonpath='{.items[0].metadata.name}')kubectl exec -it $POD_NAME -n $POD_NAMESPACE -- /nginx-ingress-controller --version
ℹ️ Create a DNS entry for hello-jss.example.com and set the CNAME to the LoadBalancer of the ingress controller Service. Replace example.com with a domain name that you have access to.
Save the following YAML, make changes to the domain name as needed and create an ingress by applying the YAML.
apiVersion: networking.k8s.io/v1kind: Ingressmetadata:name: hello-jss-ingressnamespace: jss-academyannotations:nginx.ingress.kubernetes.io/rewrite-target: /$1spec:rules:- host: hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEhttp:paths:- path: /pathType: Prefixbackend:service:name: hello-jss-svcport:number: 8080
Running kubectl -n jss-academy get Ingress will display the ingress details. It may take a few seconds for the Ingress resource to show the address. To test , simply run curl http://hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAME to see
Hello, world!Version: 1.0.0Hostname: hello-jss-app-b464dc64-mb66w
The application is deployed with a replica of 3, so if you keep running the curl you will see the hostname change on every run.
Login to TLS Protect for Kubernetes and click on the Ingresses tab. The Ingress that we created just now, will be displayed with High Severity and as Insecure
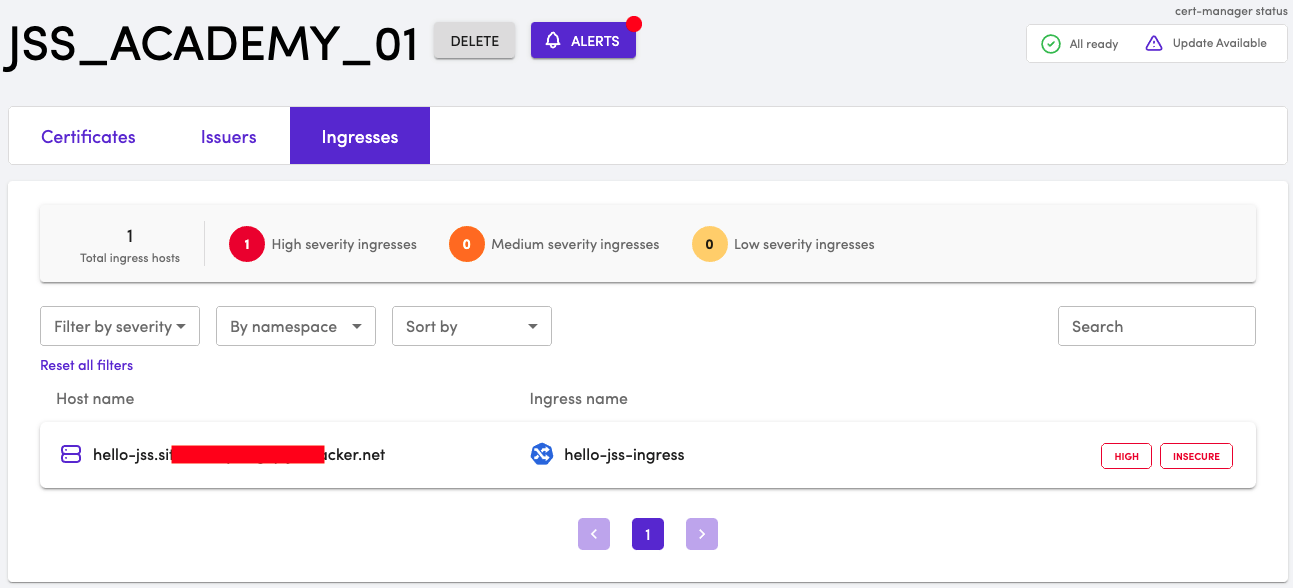
If you have connected TLS Protect for Kubernetes to a cluster that already has Ingresses, you will see them in the dashboard. If there are Ingresses that are not secured, TLS Protect for Kubernetes will help discover them. In this course, we have only one Ingress. Click on the Ingress to view the details. TLS Protect for Kubernetes provides additional details about this Ingress. The ingress is NOT policy compliant. It is flagged because TLS configuration is missing.
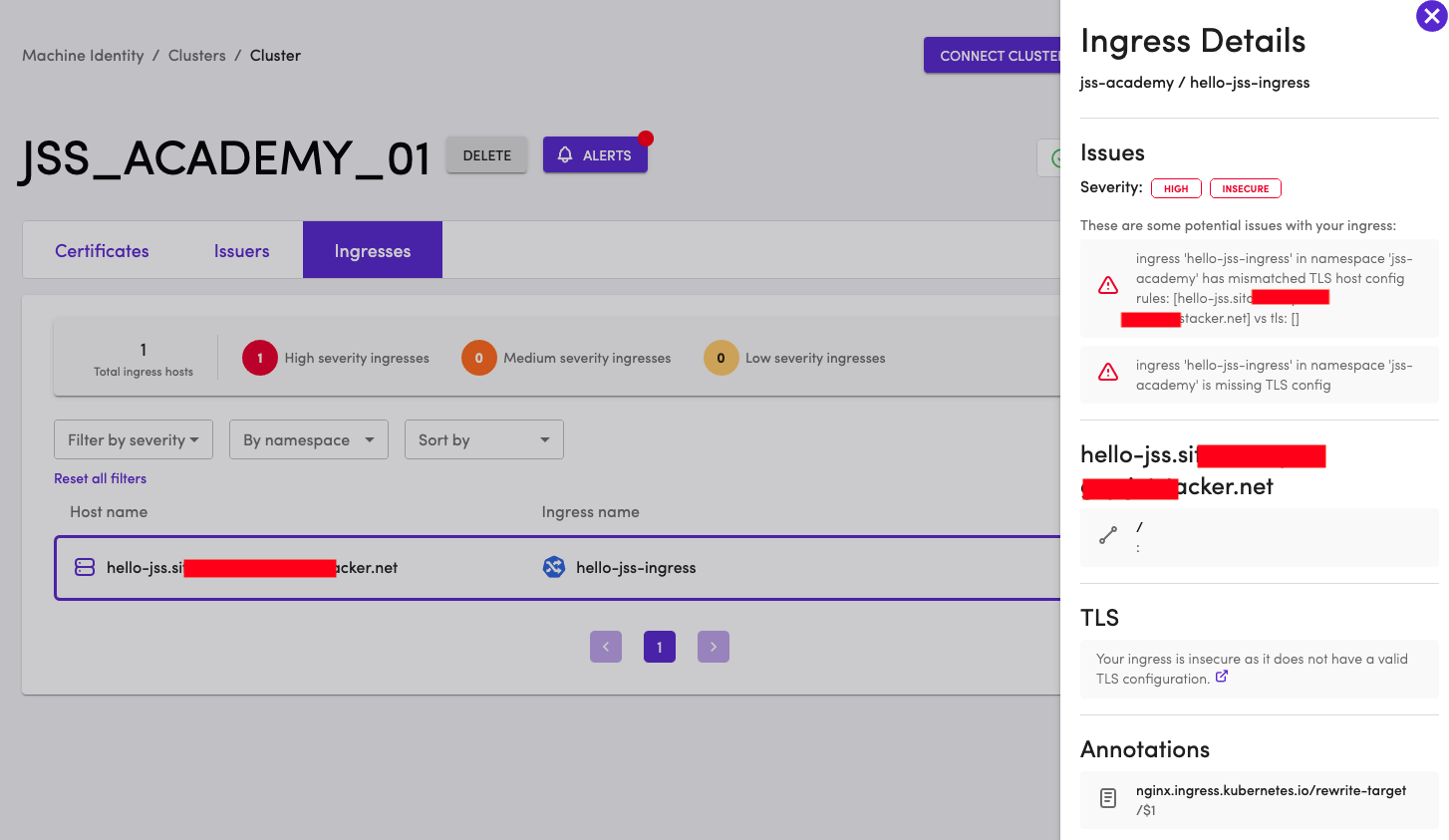
In the next chapter, let's secure the Ingress with a certificate that will be managed by TLS Protect for Kubernetes.
