Venafi TLS Protect for Kubernetes
Securely manage TLS, mTLS and SPIFFE machine identity activity in Kubernetes
Venafi TLS Protect for Kubernetes provides end-to-end machine identity management for Kubernetes and OpenShift. It comprises the Venafi TLS Protect for Kubernetes Control Plane and a suite of supporting in-cluster components. TLS Protect for Kubernetes provides your organization with automated discovery, observability, control and consistency of cloud native machine identities.
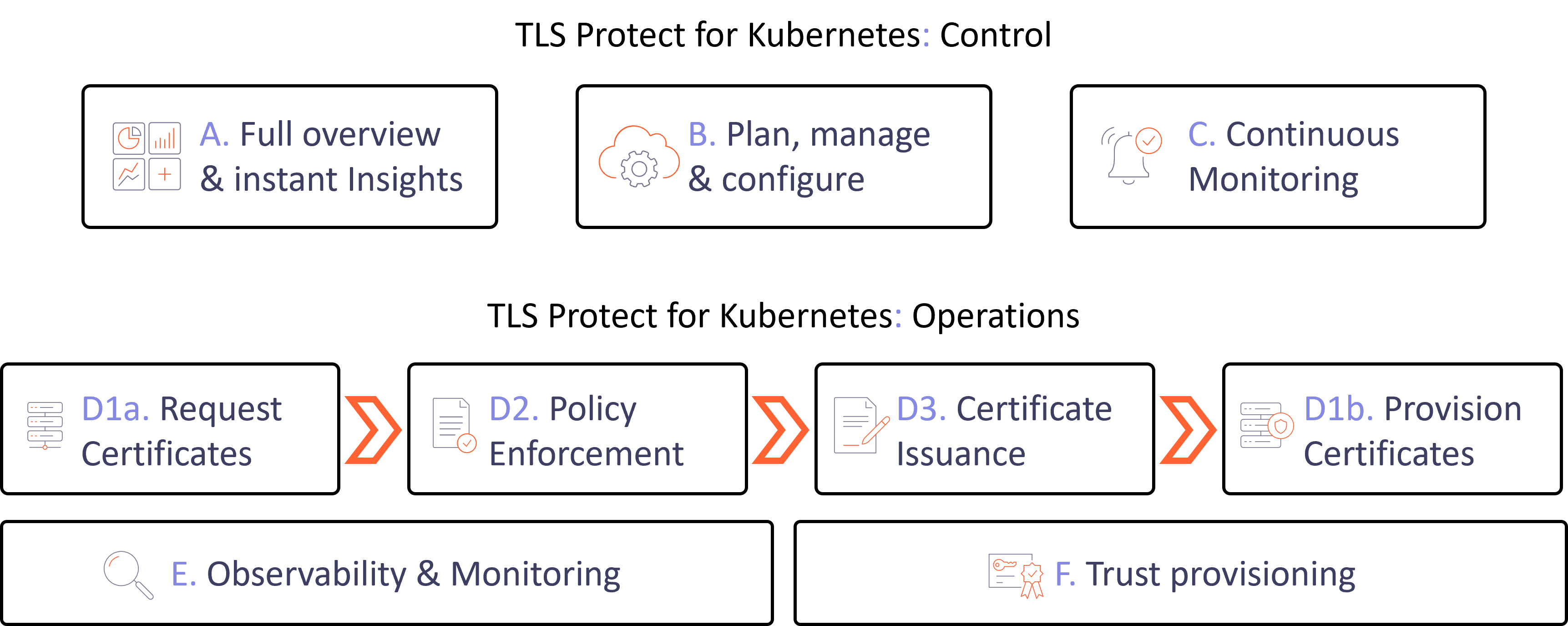
Control features

- A. Full overview & instant Insights:
- discover and view all machine identities
- analyze and triage errors, issues and risks
- B. Plan, manage & configure:
- centralized policy control
- build and enforce business processes
- C. Continuous Monitoring:
- be notified before a security issue or outage occurs
More info:
Operational capabilities
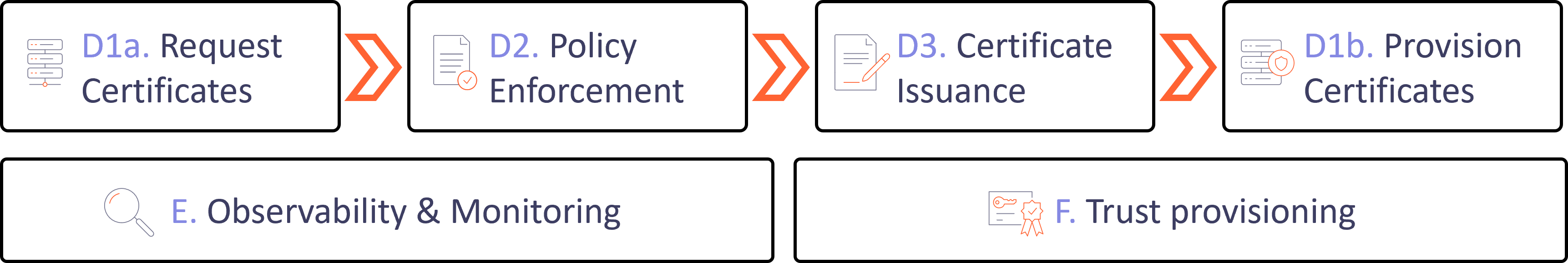
- D. Certificate Automation: Provide applications with a trusted proof of their identity
- D1. Request and Provision Certificates:
- automatically provision issued certificates
- automatically renew certificates
- remove the risk of human error during issuance and renewal
- D2. Policy Enforcement:
- ensure requested certificates meet minimum security requirements
- prevent applications from obtaining unauthorized certificates
- D3. Certificate Issuance:
- integrate with certificate authorities to sign certificates
- use signature as proof of machine identity validity
- D1. Request and Provision Certificates:
- E. Observability & Monitoring:
- view all the TLS certificates in your organization
- the certificate details provide insights into security and outage risks
- continuous monitoring and alerting makes sure we are notified in case of a security issue or outage
- F. Trust provisioning:
- provide applications with CA certificates that they must trust
- enabling rapid updates in case of compromise
More info:
Certificate Automation
Provide applications with a trusted proof of their identity.
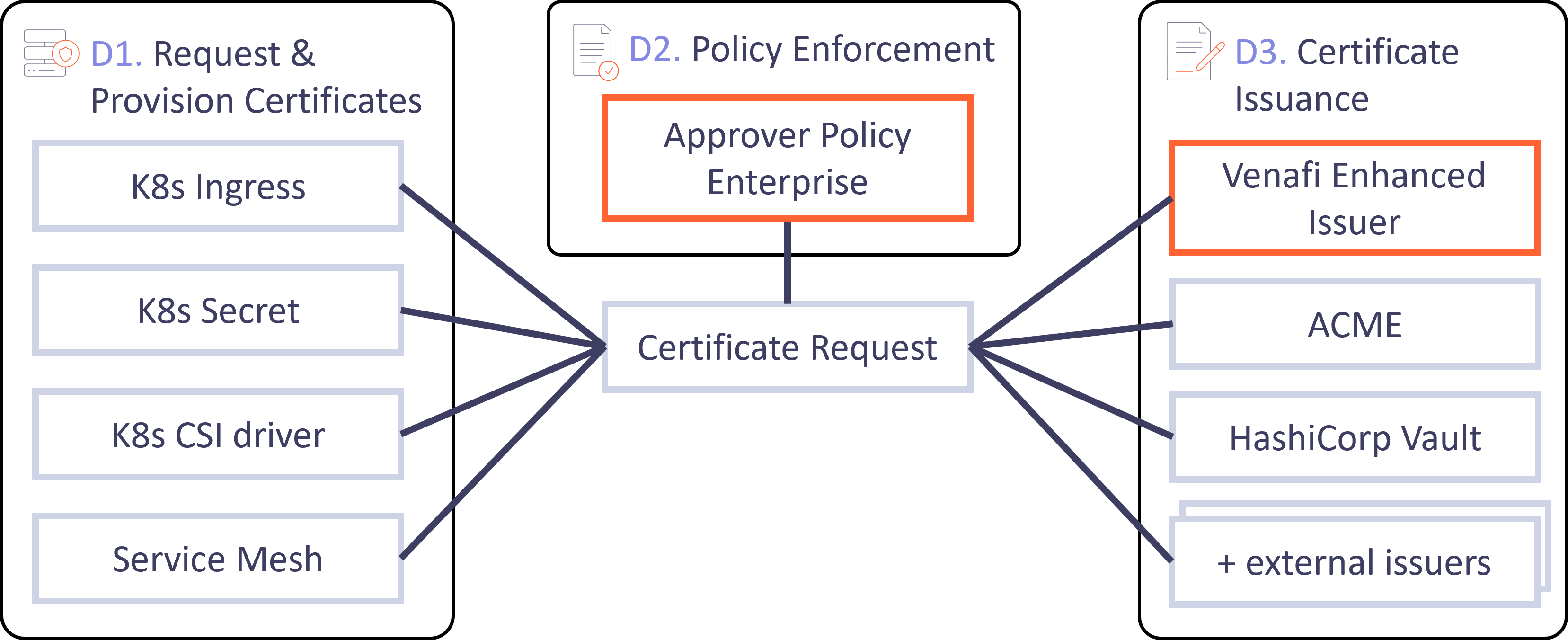
D1. Request and Provision Certificates
- Kubernetes Secret, Ingress & Gateway: cert-manger Certificate resources can be used to generate a private key stored in a Kubernetes secret and use that key to create a CertificateRequest resource. Instead of directly creating Certificate resources, it is possible to create Certificate resources based on annotations that you add to your Ingress resources. ↪ More info: Certificate resources ↪ More info: Ingress resources ↪ More info: Gateway resources
- Kubernetes CSI driver: to prevent storing private key data in Kubernetes Secrets in the cluster state, they can be generated locally inside a container thanks to our CSI driver ↪ More info: CSI Driver (1) and CSI Driver (2) ↪ More info: CSI Driver SPIFFE
- Kubernetes Service Mesh: in a Service Mesh, each service has its own identity and thus has its own Certificate. Thanks to each service having a certificate, inter-service communication can be mTLS secured. cert-manager supports requesting and provisioning certificates for multiple service mesh providers ↪ More info: Install Istio CSR and Istio CSR
D2. Policy Enforcement
- Before a Certificate Request is signed, we have to validate whether the requested certificate complies with the security policies for this specific context and requester. ↪ More info: Install and Configure approver-policy-enterprise
D3. Certificate Issuance
- For clients to trust our signed certificate, it has to be signed by a CA that is trusted by these clients. The TLS Protect for Kubernetes solution supports multiple integrations with local/ remote/ public CAs to sign certificate requests. The Venafi Enhanced Issuer uses the CAs configured through the Venafi Control plane to sign Certificate Request. ↪ More info: Install and Configure venafi-enhanced-issuer ↪ More info: OSS Issuers
Observability and monitoring
The TLS Protect for Kubernetes Agent communicates the Kubernetes machine identity state with the Venafi Control Plane. The component extends the observability and monitoring capabilities of the Venafi Control Plane to the Kubernetes cluster on which it is installed.
More info:
Trust provisioning
The workloads in the cluster also have to trust other services within or outside of the cluster. To make sure we are trusting all critical services and not trusting any malicious services, it is crucial to have an up-to-date list of trusted certificates available to each client. The trust-manager project provides a solution for provisioning trusted CA certificates across all workloads in your cluster.
More info:
