Requesting a policy compliant certificate
Creating a certificate
Before we request a certificate, let's make sure that the issuer we created in the previous course is available. Click on the Issuers tab in TLS Protect for Kubernetes. The academy-issuer that we created should still be available.
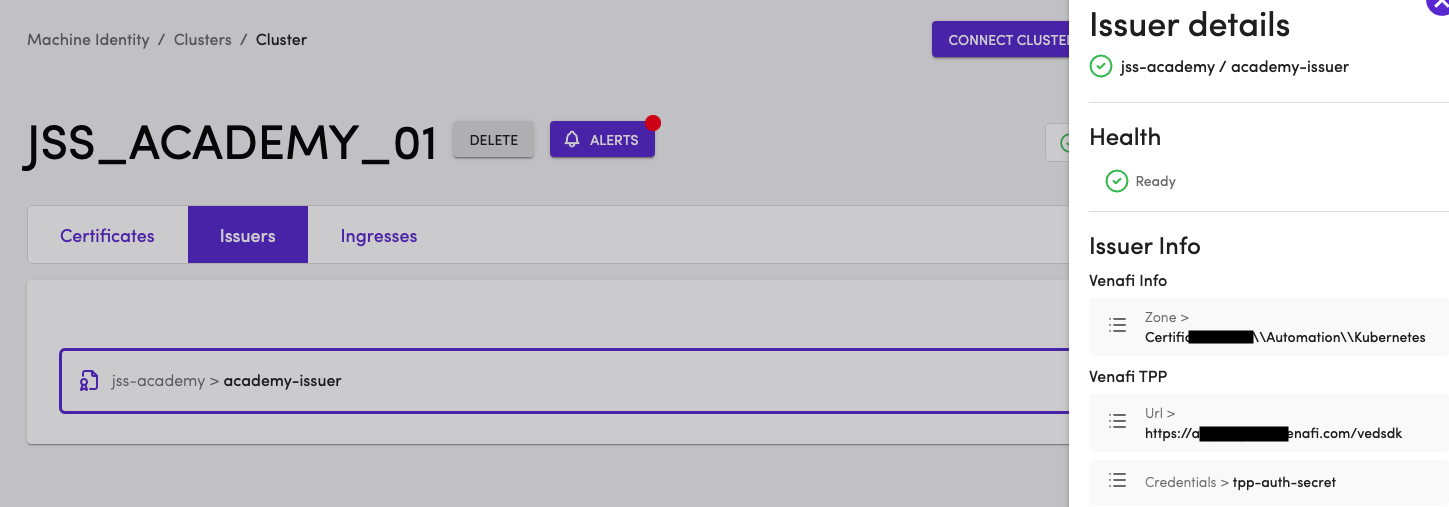
The certificate we need for securing the Ingress will be requested from the issuer academy-issuer. As discussed previously, there are many kinds of issuers and academy-issuer is the name of the issuer. The configuration of academy-issuer will tell us where the certificate will come from. If you are unsure about what the configuration of academy-issuer , click on academy-issuer in the Issuers page for details.
Save the following YAML, make changes to the domain name as needed to create a certificate and apply it.
apiVersion: cert-manager.io/v1kind: Certificatemetadata:name: hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEnamespace: jss-academyspec:secretName: hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEdnsNames:- hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEcommonName: hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEissuerRef:name: academy-issuerkind: Issuer
For more details about the Certificate resource and its usage, checkout documentation here
Navigate to the TLS Protect for Kubernetes Dashboard's Certificate tab and you will see the newly requested certificate in the dashboard.
Note
TLS Protect for Kubernetes agent running in the cluster periodically sends data to TLS Protect for Kubernetes. It may take a browser refresh to see the new certificate on the dashboard
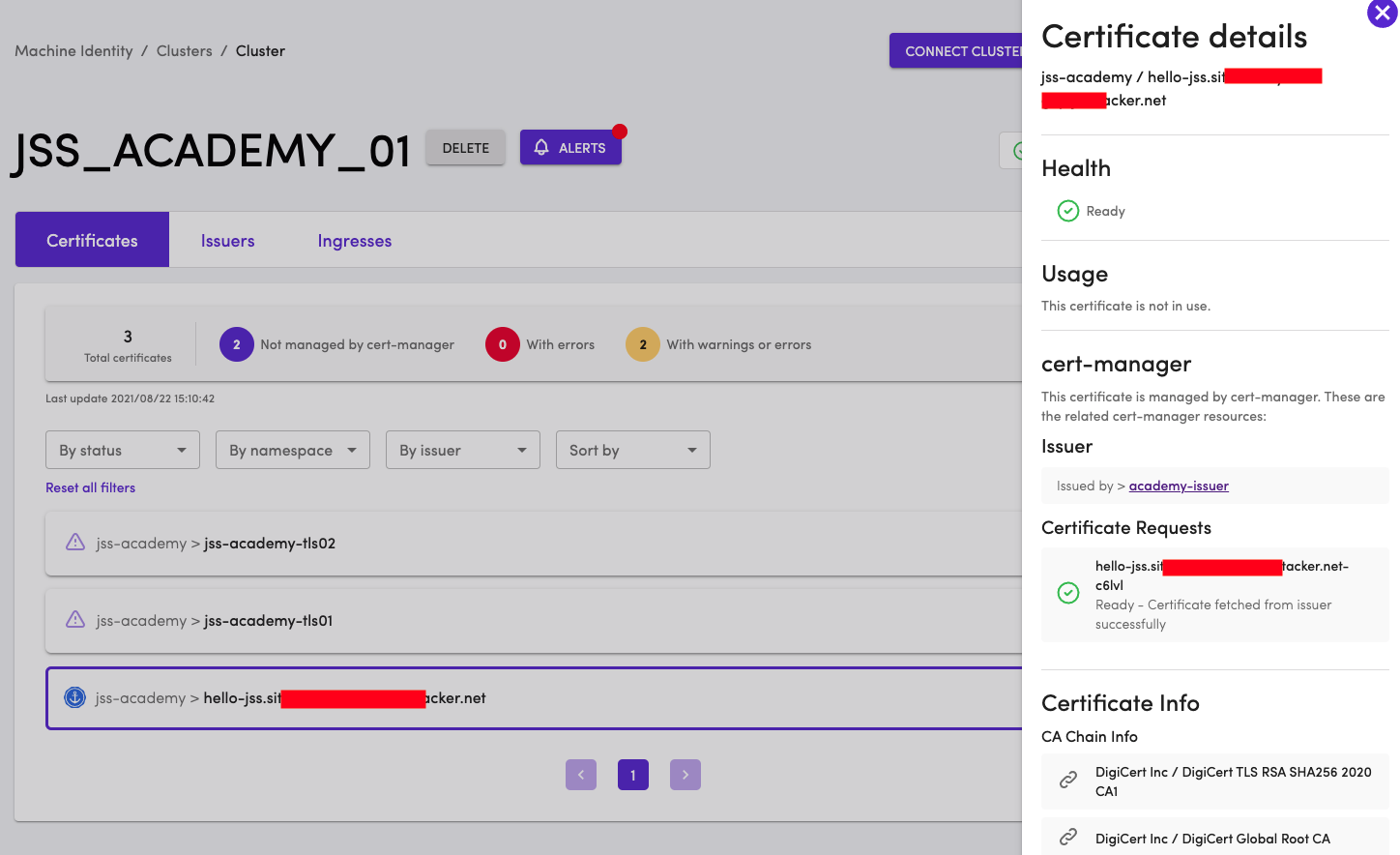
Inspect the certificate details. In addition to providing details about who issued the certificate, the Certificate Info will provide details about the CA who issued the certificate, along with all the public details about the certificate. If any of the policies are in violation, the Health of the Certificate will be appropriately flagged. In this example, the Health shows Ready
Note
The Certificate Details also says that the certificate is not in use. Our next step is to make sure that this certificate is used by the Ingress
Updating the Ingress
We created an Ingress earlier and tested it as well. We know from TLS Protect for Kubernetes that the ingress we created is not policy compliant and needs to be secured.
Save the following YAML, make changes to the domain name as needed to update the Ingress and apply it.
Note
This will update the Ingress that we already have. The additional TLS section is now added to the Ingress to use the certificate we created.
apiVersion: networking.k8s.io/v1kind: Ingressmetadata:name: hello-jss-ingressnamespace: jss-academyannotations:nginx.ingress.kubernetes.io/rewrite-target: /$1spec:tls:- hosts:- hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEsecretName: hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMErules:- host: hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAMEhttp:paths:- path: /pathType: Prefixbackend:service:name: hello-jss-svcport:number: 8080
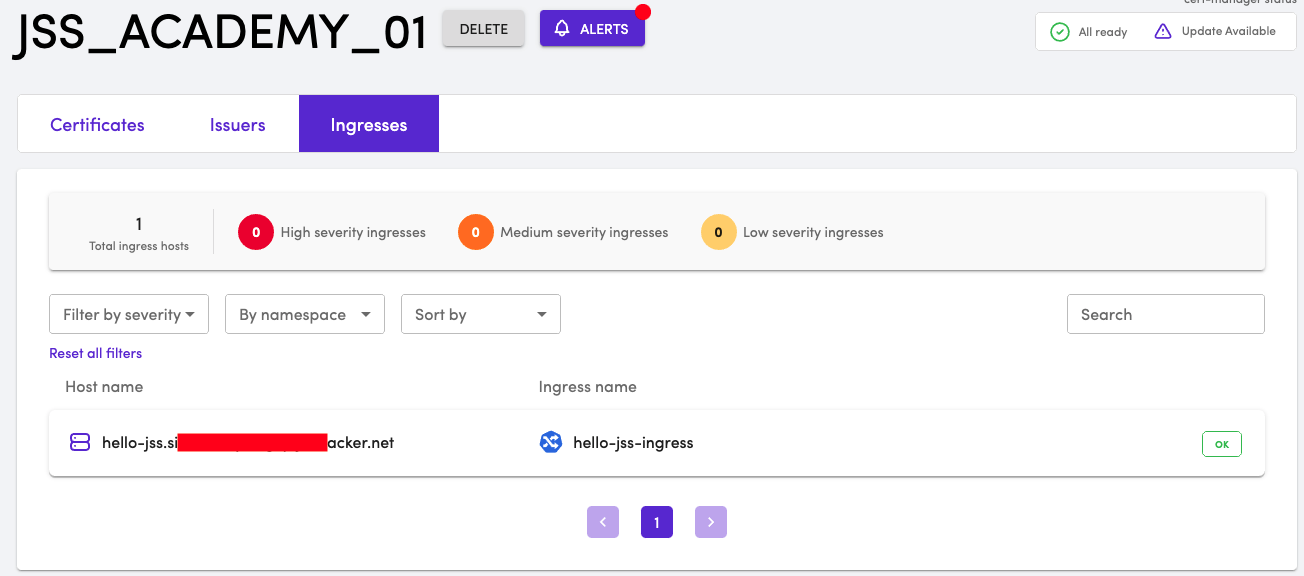
Inspect the Ingress resource in TLS Protect for Kubernetes Dashboard. The status is updated to OK. Additionally clicking on the ingress resource provide TLS information.
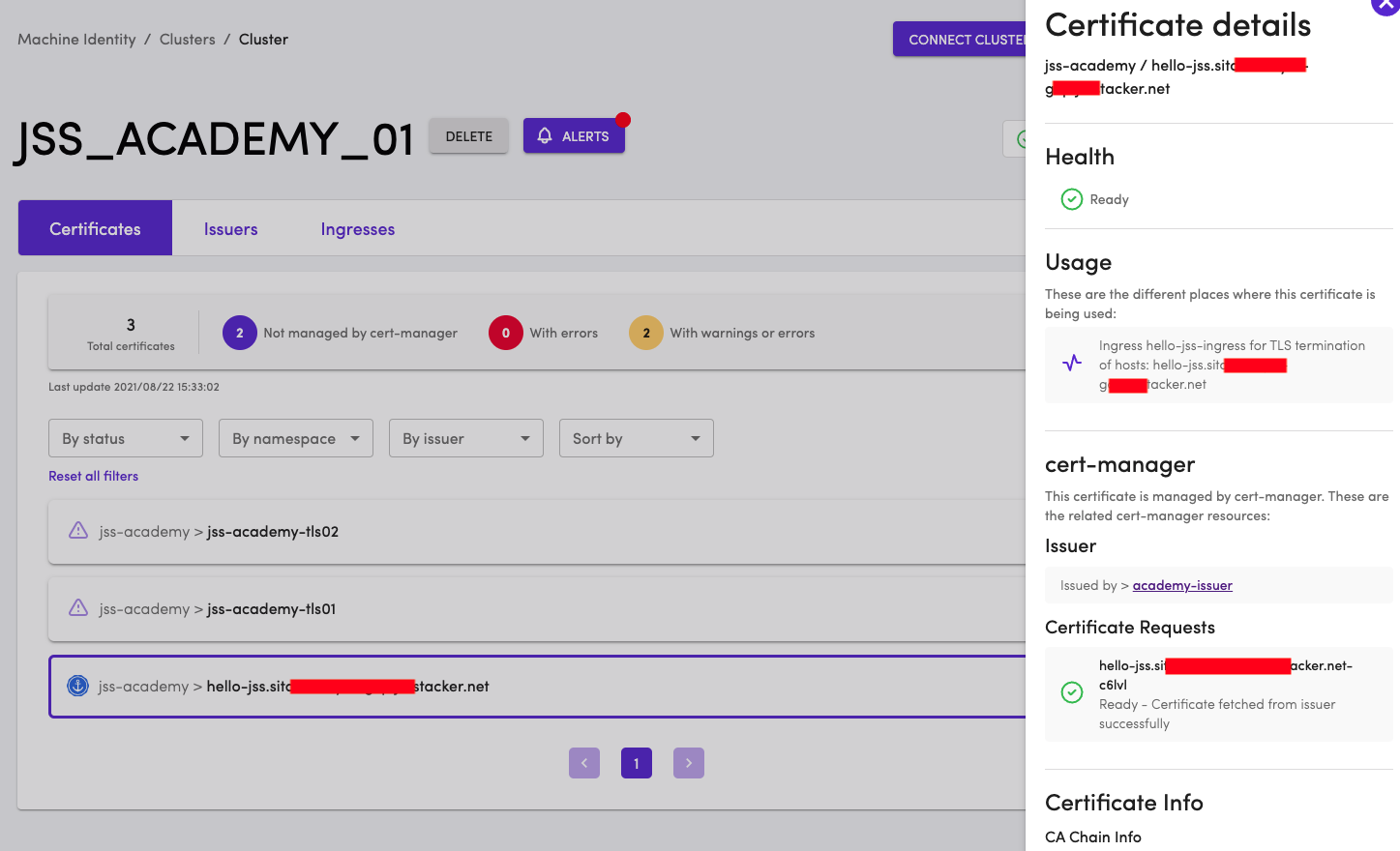
The Certificate resource is also updated to show the usage information. The certificate is marked as in-use by Ingress in the Certificate details page.
The sample application that we deployed is not longer accessible via HTTP. Try accessing via http and you will see an error. To test , simply run curl https://hello-jss.REPLACE_WITH_YOUR_DOMAIN_NAME to see
Hello, world!Version: 1.0.0Hostname: hello-jss-app-b464dc64-mb66w
Access the application via the browser and inspect the certificate details as well.
