Installing cert-discovery-venafi
Prerequisites
This assumes that you have access to a Venafi Trust Protection Platform (TPP) instance. cert-discovery-venafi is known to work with Venafi TPP 20.4 and above.
To be able to use cert-discovery-venafi, you need to have access to a Kubernetes cluster. cert-discovery-venafi tool will require access to all Secret resources in your cluster.
Assumptions
Before continuing, make sure you have kubectl, helm, and vcert installed on your machine.
Docker Images
The Docker images for cert-discovery-venafi are published to a private Docker registry at eu.gcr.io/jetstack-secure-enterprise/cert-discovery-venafi and there is a Helm chart published to a private Helm registry at oci://eu.gcr.io/jetstack-secure-enterprise/charts/cert-discovery-venafi. The Docker images are meant for the linux/amd64 architecture.
There are also FIPS compliant Docker images available at eu.gcr.io/jetstack-secure-enterprise/cert-discovery-venafi-fips and these have the same version tags as the main Docker images.
Configure access to the enterprise registry
🔑 Follow the instructions in Access to enterprise components to enable access to the artifacts required for this component. Use jetstack-secure as the namespace.
Get an access token from Venafi TPP
In this step, we will be creating a token by navigating the Venafi TPP UI. cert-discovery-venafi requires an access token to communicate with your Venafi TPP instance. In this step, it is assumed that you have access to a username and password to be able to log into your Venafi TPP instance.
We want to navigate to the Venafi TPP "API Application" page:
https://your-tpp-url/aperture/application-integrations/
Open the default API Application "VCert SDK", and check that it has the right scopes. The required scopes are certificates:manage,discover. For example, in the following screenshot, we can see that "Managed" and "Discover" are already checked:
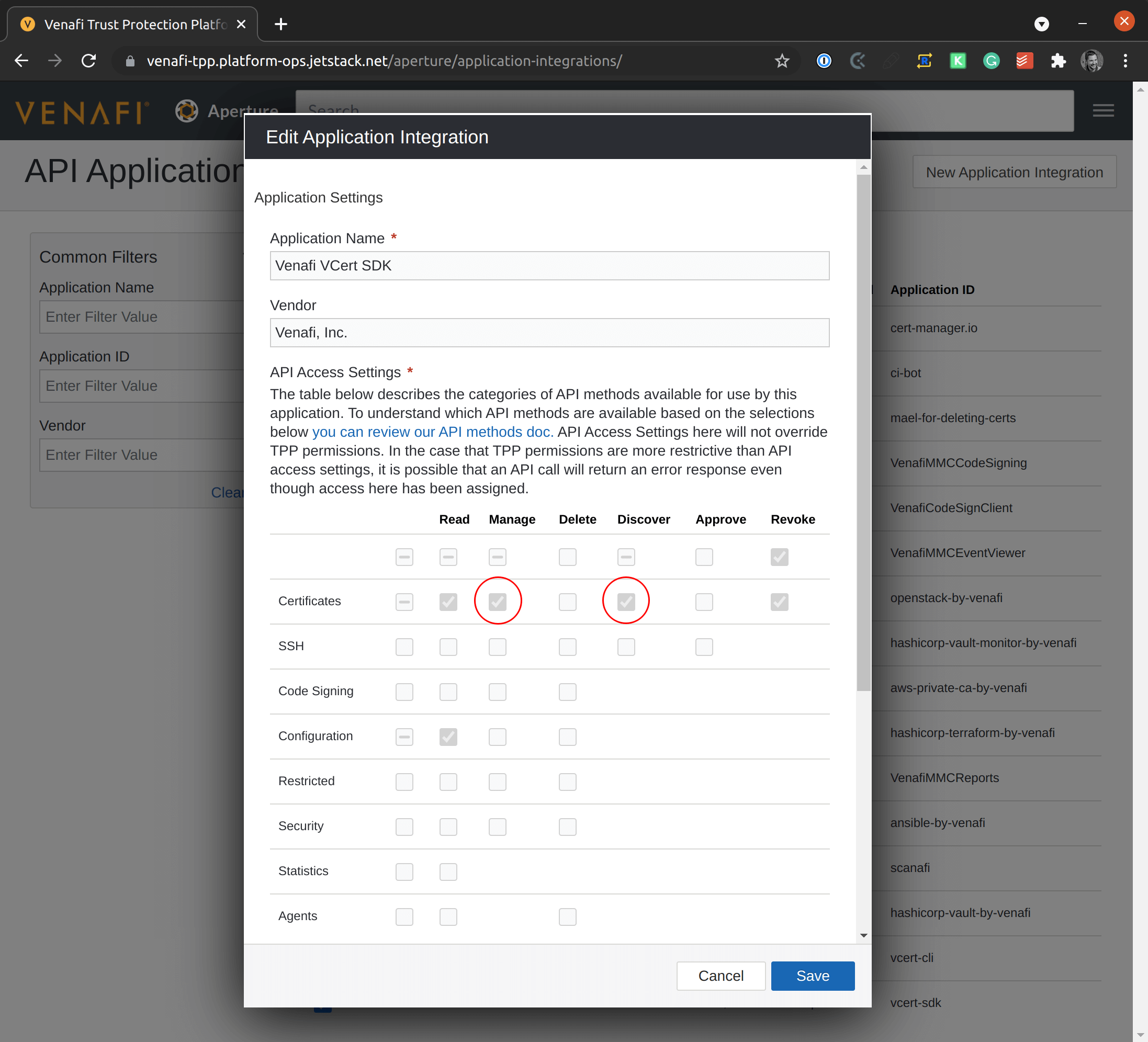
Each API application has an associated "application ID", also called "client ID". This "application ID" is visible in the API Application page. In the case of "VCert SDK", the "client ID" is vcert-sdk. You will use this value to set the variable VENAFI_TPP_CLIENT_ID.
Let us set the a few variables to be used in the next steps:
VENAFI_TPP_URL=https://your-tpp-url/vedsdkVENAFI_TPP_USERNAME=usernameVENAFI_TPP_PASSWORD=passwordVENAFI_TPP_CLIENT_ID=vcert-sdkVENAFI_TPP_ZONE='Your\Zone'
Note: the term "zone" as used in the below VENAFI_TPP_ZONE variable is equivalent to the term "policy folder". The term "policy folder" is often used in Venafi TPP, and the term "zone" is the term used in Venafi Cloud.
You can now request an access token with the following command:
TOKEN=$(vcert getcred -u $VENAFI_TPP_URL \--username $VENAFI_TPP_USERNAME \--password $VENAFI_TPP_PASSWORD \--client-id=$VENAFI_TPP_CLIENT_ID \--scope=certificate:manage,discover \--format json | jq -r .access_token)
Finally, create the Kubernetes Secret that will contain the access token:
kubectl create secret generic access-token \-n jetstack-secure \--from-literal=access-token="$TOKEN"
Deploying cert-discovery-venafi using Helm
You can now install cert-discovery-venafi using Helm:
helm upgrade --install cert-discovery-venafi \oci://eu.gcr.io/jetstack-secure-enterprise/charts/cert-discovery-venafi \--registry-config <(jsctl registry auth output --format=dockerconfig) \--version v0.2.0 \--create-namespace \--namespace jetstack-secure \--set 'imagePullSecrets[0].name=jse-gcr-creds' \--set url="$VENAFI_TPP_URL" \--set zone="$VENAFI_TPP_ZONE"
If your TPP instance is served by a certificate signed by your company's private CA, you will first need to store the CA certificate (there may be multiple) in PEM encoded format in a ConfigMap. Imagining that the CA certificates used to trust your TPP instance are available in the file tpp-ca-certificates.crt, then create the ConfigMap with the following command:
kubectl create configmap tpp-ca-certificates -n jetstack-secure \--from-file=ca.crt=tpp-ca-certificates.crt
The next step is to run the above helm upgrade --install command with an additional argument:
--set caBundle.configMap.name=tpp-ca-certificates
Note that Helm 3.8 or above is required to be able to use the oci:// protocol. If you are using Helm 3.7, you can still use the feature by setting HELM_EXPERIMENTAL_OCI=1.
Use FIPS compliant Docker images
You can use the FIPS Docker compliant images by overriding the controllerManager.manager.image.repository value of the Helm chart. E.g.:
VERSION=0.2.0helm upgrade cert-discovery-venafi oci://eu.gcr.io/jetstack-secure-enterprise/charts/cert-discovery-venafi \--registry-config <(jsctl registry auth output --format=dockerconfig) \--wait \--install \--create-namespace \--namespace jetstack-secure \--version $VERSION \--set 'imagePullSecrets[0].name=jse-gcr-creds' \--set controllerManager.manager.image.repository=eu.gcr.io/jetstack-secure-enterprise/cert-discovery-venafi-fips
Verifying that certificates are being pushed to Venafi TPP
After installing, cert-discovery-venafi starts importing TLS Secrets into your Venafi TPP instance under the policy folder that you specified with the variable VENAFI_TPP_ZONE. You can open the Venafi TPP UI to check that the certificates have been imported.
